Many companies have started their journey to the cloud with migrating a handful of existing applications to the cloud, firstly to quickly deliver business value for adopting cloud, and secondly to pilot some of their existing applications and workloads on the cloud. Other companies could be adopting a multi-cloud strategy, justifying multi-cloud adoption for business continuity. Lastly, we have companies born in the cloud, with cloud native applications developed for the cloud.
When the returns of cloud adoption are justifiable, and aligns to long-term business goals, the next step and best practice for companies would be to assess adopting the Enterprise-Scale Landing Zone, for future-proofing their cloud environment, while ensuring good control and governance. There are a few reasons,
- Cloud Governance guardrails the cloud environment, securing it from accidental configurations or deployments, enhances reliability and auditability.
- Lower costs of adopting or refactoring Landing Zone.
- Start-Small-Think-Big: A security-first, test driven development approach, minimizes exponential operational costs as the cloud environment scales.
Challenges with adopting Enterprise-Scale Landing Zone would be how to test it, what if Infrastructure-as-code were not developed before, and how to transition to the landing zone with minimal downtime and costs.
This solution architecture models a staging and production environment that uses DevSecOps to transition apps in the Landing Zone with the Strangler Fig pattern. With the Strangler Fig pattern, small incremental steps to decouple and refactor production workloads, mitigates risks in software delivery, while the foundation code for Infrastructure-as-Code and automated tests are being developed.
In this scenario,
- The cloud infrastructure and services was manually setup, Infrastructure-as-Code was not implemented.
- DevOps was used to deploy applications to existing production environment, but did not include security scanning and/or automated tests.
- The applications have significant complexity, with multiple microservices that are decoupled from each other.
- Contoso is an enterprise with global offices, managed independently from the rest of the regions. They want to pilot the first Landing Zone at their Headquarters.
Architecture
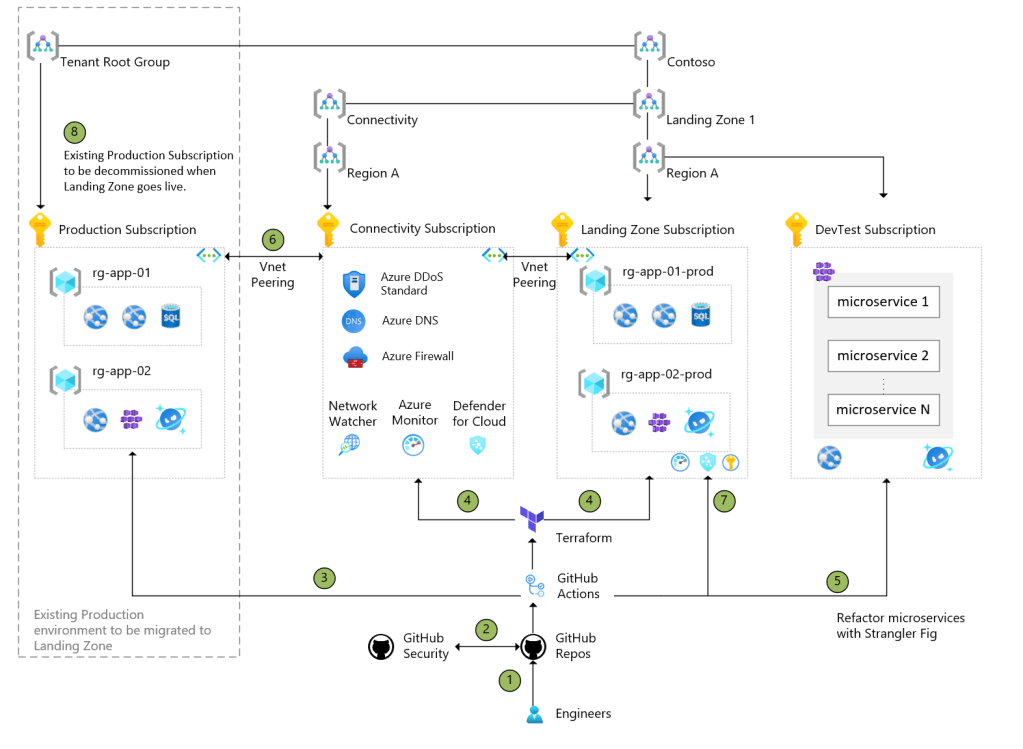
Data Flow
- With test driven development, engineers checks in code changes for unit tests, application code, infrastructure-as-code, policy-as-code.
- GitHub Advanced Security analyses all the branches, looking for hardcoded secrets and dependency vulnerabilities. If a vulnerability is detected (for example, a dependency to a deprecated non-secure package), GitHub sends alerts to the organization or repository owners and maintainers. GitHub Dependabot creates a new branch in the repository, automatically upgrades the old dependency to a secure version, and creates a pull request (PR) with the upgraded dependency. The PR requires manual approval.
- GitHub Actions are configured to build, test, and scans for code quality, and scans for vulnerability with CodeQL.
- Test Driven Development for infrastructure are developed. Terraform provisions and modifies resources for each environment, tailoring size, instance count, and other properties.
- Applications deployed to staging environment for development and tests. There could be two types of applications
- Simple Applications can be tested and deployed to production environment with minimal code changes.
- Complex Applications can be migrated in phases with the Strangler Fig pattern. This application will be running in both the existing and new landing zone subscriptions.
- VNet peering is enabled between existing and new landing zone subscriptions to enable application to route calls to appropriate backend services, as prioritized for migration. Such an approach may introduce latency to the application, and needs to planned appropriately.
- When applications are ready to go live, the GitHub Actions will be enabled to continuously deploy updates to the new landing zone.
- When all of the applications in existing landing zone is migrated to the new landing zone, the old subscription can be decommissioned.
Components
- Visual Studio Code extensions support Azure Boards and GitHub integration. Associating Azure Boards work items with GitHub repos ties requirements to code, driving the development loop forward.
- GitHub is a code hosting platform for version control and collaboration. A GitHub source-control repository contains all project files and their revision history. Developers can work together to contribute, discuss, and manage code in the repository.
- GitHub Actions provides a suite of build and release workflows, covering CI, automated testing, and container deployments.
- GitHub Advanced Security. Advanced Security provides features to improve and maintain the quality of your code in three major areas. It requires an additional license.
- Code scanning: Search for potential security vulnerabilities and coding errors in your code.
- Secret scanning: Detect secrets (for example, keys and tokens) that have been checked into the repository.
- Dependency review: Show the full impact of changes to dependencies and see details of any vulnerable versions before you merge a PR.
- CodeQL: An analysis engine used by developers to automate security checks.
- Terraform is a third-party product developed by HashiCorp that allows infrastructure automation on Azure, as well as on other environments.
- Azure Key Vault securely stores and tightly controls access to secrets like API keys, passwords, and certificates. For more information about Key Vault in DevOps scenarios, see DevSecOps in Azure and DevSecOps in GitHub.
- Azure Active Directory (Azure AD) enterprise identity platform provides single sign-on and multifactor authentication to govern user access. A single Azure AD can manage identity for all environments across subscriptions. Azure role-based access control (Azure RBAC) restricts access to protected resources, preventing unauthorized or inadvertent modification of production resources.
